About the CoMSES Model Library more info
Our mission is to help computational modelers develop, document, and share their computational models in accordance with community standards and good open science and software engineering practices. Model authors can publish their model source code in the Computational Model Library with narrative documentation as well as metadata that supports open science and emerging norms that facilitate software citation, computational reproducibility / frictionless reuse, and interoperability. Model authors can also request private peer review of their computational models. Models that pass peer review receive a DOI once published.
All users of models published in the library must cite model authors when they use and benefit from their code.
Please check out our model publishing tutorial and feel free to contact us if you have any questions or concerns about publishing your model(s) in the Computational Model Library.
We also maintain a curated database of over 7500 publications of agent-based and individual based models with detailed metadata on availability of code and bibliometric information on the landscape of ABM/IBM publications that we welcome you to explore.
Displaying 10 of 376 results for "Huw Vasey" clear search
Potato late blight model
Francine Pacilly | Published Friday, April 13, 2018The purpose of the model is to simulate the spatial dynamics of potato late blight to analyse whether resistant varieties can be used effectively for sustainable disease control. The model represents an agricultural landscape with potato fields and data of a Dutch agricultural region is used as input for the model. We simulated potato production, disease spread and pathogen evolution during the growing season (April to September) for 36 years. Since late blight development and crop growth is weather dependent, measured weather data is used as model input. A susceptible and late blight resistant potato variety are distinguished. The resistant variety has a potentially lower yield but cannot get infected with the disease. However, during the growing season virulent spores can emerge as a result of mutations during spore production. This new virulent strain is able to infect the resistant fields, resulting in resistance breakdown. The model shows how disease severity, resistance durability and potato yield are affected by the fraction of fields across a landscape with a disease-resistant potato variety.
Peer reviewed Zimbabwe Agro-Pastoral Management Model (ZAPMM): Musimboti wevanhu, zvipfuo nezvirimwa
MV Eitzel Solera Kleber Tulio Neves Jon Solera Kenneth B Wilson Abraham Mawere Ndlovu Aaron C Fisher André Veski Oluwasola E Omoju Emmanuel Mhike Hove | Published Tuesday, June 19, 2018This model has been created with and for the researcher-farmers of the Muonde Trust (http://www.muonde.org/), a registered Zimbabwean non-governmental organization dedicated to fostering indigenous innovation. Model behaviors and parameters (mashandiro nemisiyano nedzimwe model) derive from a combination of literature review and the collected datasets from Muonde’s long-term (over 30 years) community-based research. The goals of this model are three-fold (muzvikamu zvitatu):
A) To represent three components of a Zimbabwean agro-pastoral system (crops, woodland grazing area, and livestock) along with their key interactions and feedbacks and some of the human management decisions that may affect these components and their interactions.
B) To assess how climate variation (implemented in several different ways) and human management may affect the sustainability of the system as measured by the continued provisioning of crops, livestock, and woodland grazing area.
C) To provide a discussion tool for the community and local leaders to explore different management strategies for the agro-pastoral system (hwaro/nzira yekudyidzana kwavanhu, zvipfuo nezvirimwa), particularly in the face of climate change.
Peer reviewed FishMob: Interactions between fisher mobility and spatial resource heterogeneity
Emilie Lindkvist | Published Wednesday, October 16, 2019 | Last modified Tuesday, June 23, 2020Migration or other long-distance movement into other regions is a common strategy of fishers and fishworkers living and working on the coast to adapt to environmental change. This model attempts to understand the general dynamics of fisher mobility for over larger spatial scales. The model can be used for investigating the complex interplay that exists between mobility and fish stock heterogeneity across regions, and the associated outcomes of mobility at the system level.
The model design informed by the example of small-scale fisheries in the Gulf of California, Mexico but implements theoretical and stylized facts and can as such be used for different archetypical cases. Our methodological approach for designing the model aims to account for the complex causation, emergence and interdependencies in small-scale fisheries to explain the phenomenon of sequential overexploitation, i.e., overexploiting one resource after another. The model is intended to be used as a virtual laboratory to investigate when and how different levels of mobile fishers affect exploitation patterns of fisheries resources.
While the world’s total urban population continues to grow, not all cities are witnessing such growth, some are actually shrinking. This shrinkage causes several problems to emerge including population loss, economic depression, vacant properties and the contraction of housing markets. Such problems challenge efforts to make cities sustainable. While there is a growing body of work on study shrinking cities, few explore such a phenomenon from the bottom up using dynamic computational models. To overcome this issue this paper presents an spatially explicit agent-based model stylized on the Detroit Tri-county area, an area witnessing shrinkage. Specifically, the model demonstrates how through the buying and selling of houses can lead to urban shrinkage from the bottom up. The model results indicate that along with the lower level housing transactions being captured, the aggregated level market conditions relating to urban shrinkage are also captured (i.e., the contraction of housing markets). As such, the paper demonstrates the potential of simulation to explore urban shrinkage and potentially offers a means to test polices to achieve urban sustainability.
Hybrid agent-based methodology for testing response protocols
Fernando Sancho Caparrini | Published Wednesday, February 03, 2021In recent years we have seen multiple incidents with a large number of people injured and killed by one or more armed attackers. Since this type of violence is difficult to predict, detecting threats as early as possible allows to generate early warnings and reduce response time. In this context, any tool to check and compare different action protocols can be a further step in the direction of saving lives. Our proposal combines features from continuous and discrete models to obtain the best of both worlds in order to simulate large and crowded spaces where complex behavior individuals interact. With this proposal we aim to provide a tool for testing different security protocols under several emergency scenarios, where spaces, hazards, and population can be customized. Finally, we use a proof of concept implementation of this model to test specific security protocols under emergency situations for real spaces. Specifically, we test how providing some users of a university college with an app that informs about the type and characteristics of the ongoing hazard, affects in the safety performance.
Peer reviewed Modelling Agricultural Innovations as a Social-Ecological Phenomenon
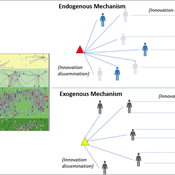
Maja Schlüter Udita Sanga | Published Thursday, November 17, 2022The goal of the AG-Innovation agent-based model is to explore and compare the effects of two alternative mechanisms of innovation development and diffusion (exogenous, linear and endogenous, non-linear) on emergent properties of food and income distribution and adoption rates of different innovations. The model also assesses the range of conditions under which these two alternative mechanisms would be effective in improving food security and income inequality outcomes. Our modelling questions were: i) How do cross-scalar social-ecological interactions within agricultural innovation systems affect system outcomes of food security and income inequality? ii) Do foreign aid-driven exogenous innovation perpetuate income inequality and food insecurity and if so, under which conditions? iii) Do community-driven endogenous innovations improve food security and income inequality and if so, under which conditions? The Ag-Innovation model is intended to serve as a thinking tool for for the development and testing of hypotheses, generating an understanding of the behavior of agricultural innovation systems, and identifying conditions under which alternated innovation mechanisms would improve food security and income inequality outcomes.
Using Agent-Based Modelling and Reinforcement Learning to Study Hybrid Threats
kpadur | Published Friday, September 20, 2024Hybrid attacks coordinate the exploitation of vulnerabilities across domains to undermine trust in authorities and cause social unrest. Whilst such attacks have primarily been seen in active conflict zones, there is growing concern about the potential harm that can be caused by hybrid attacks more generally and a desire to discover how better to identify and react to them. In addressing such threats, it is important to be able to identify and understand an adversary’s behaviour. Game theory is the approach predominantly used in security and defence literature for this purpose. However, the underlying rationality assumption, the equilibrium concept of game theory, as well as the need to make simplifying assumptions can limit its use in the study of emerging threats. To study hybrid threats, we present a novel agent-based model in which, for the first time, agents use reinforcement learning to inform their decisions. This model allows us to investigate the behavioural strategies of threat agents with hybrid attack capabilities as well as their broader impact on the behaviours and opinions of other agents.
Incentives for data sharing
Flaminio Squazzoni Federico Bianchi Thomas Klebel Tony Ross-Hellauer | Published Thursday, October 02, 2025Although beneficial to scientific development, data sharing is still uncommon in many research areas. Various organisations, including funding agencies that endorse open science, aim to increase its uptake. However, estimating the large-scale implications of different policy interventions on data sharing by funding agencies, especially in the context of intense competition among academics, is difficult empirically. Here, we built an agent-based model to simulate the effect of different funding schemes (i.e., highly competitive large grants vs. distributive small grants), and varying intensity of incentives for data sharing on the uptake of data sharing by academic teams strategically adapting to the context.
Rebel Group Protection Rackets
Gerd Wagner Luis Gustavo Nardin Kamil C. Klosek Frances Duffy | Published Wednesday, December 04, 2019System Narrative
How do rebel groups control territory and engage with the local economy during civil war? Charles Tilly’s seminal War and State Making as Organized Crime (1985) posits that the process of waging war and providing governance resembles that of a protection racket, in which aspiring governing groups will extort local populations in order to gain power, and civilians or businesses will pay in order to ensure their own protection. As civil war research increasingly probes the mechanisms that fuel local disputes and the origination of violence, we develop an agent-based simulation model to explore the economic relationship of rebel groups with local populations, using extortion racket interactions to explain the dynamics of rebel fighting, their impact on the economy, and the importance of their economic base of support. This analysis provides insights for understanding the causes and byproducts of rebel competition in present-day conflicts, such as the cases of South Sudan, Afghanistan, and Somalia.
Model Description
The model defines two object types: RebelGroup and Enterprise. A RebelGroup is a group that competes for power in a system of anarchy, in which there is effectively no government control. An Enterprise is a local civilian-level actor that conducts business in this environment, whose objective is to make a profit. In this system, a RebelGroup may choose to extort money from Enterprises in order to support its fighting efforts. It can extract payments from an Enterprise, which fears for its safety if it does not pay. This adds some amount of money to the RebelGroup’s resources, and they can return to extort the same Enterprise again. The RebelGroup can also choose to loot the Enterprise instead. This results in gaining all of the Enterprise wealth, but prompts the individual Enterprise to flee, or leave the model. This reduces the available pool of Enterprises available to the RebelGroup for extortion. Following these interactions the RebelGroup can choose to AllocateWealth, or pay its rebel fighters. Depending on the value of its available resources, it can add more rebels or expel some of those which it already has, changing its size. It can also choose to expand over new territory, or effectively increase its number of potential extorting Enterprises. As a response to these dynamics, an Enterprise can choose to Report expansion to another RebelGroup, which results in fighting between the two groups. This system shows how, faced with economic choices, RebelGroups and Enterprises make decisions in war that impact conflict and violence outcomes.
CEDSS is an agent-based model of domestic energy demand at the level of a small community.
Displaying 10 of 376 results for "Huw Vasey" clear search