About the CoMSES Model Library more info
Our mission is to help computational modelers develop, document, and share their computational models in accordance with community standards and good open science and software engineering practices. Model authors can publish their model source code in the Computational Model Library with narrative documentation as well as metadata that supports open science and emerging norms that facilitate software citation, computational reproducibility / frictionless reuse, and interoperability. Model authors can also request private peer review of their computational models. Models that pass peer review receive a DOI once published.
All users of models published in the library must cite model authors when they use and benefit from their code.
Please check out our model publishing tutorial and feel free to contact us if you have any questions or concerns about publishing your model(s) in the Computational Model Library.
We also maintain a curated database of over 7500 publications of agent-based and individual based models with detailed metadata on availability of code and bibliometric information on the landscape of ABM/IBM publications that we welcome you to explore.
Displaying 10 of 1170 results for "Aad Kessler" clear search
The S-uFUNK Model
Davide Secchi | Published Friday, March 17, 2023This version 2.1.0 of the uFunk model is about setting a business strategy (the S in the name) for an organization. A team of managers (or executives) meet and discuss various options on the strategy for the firm. There are three aspects that they have to agree on to set the strategic positioning of the organization.
The discussion is on market, stakeholders, and resources. The team (it could be a business strategy task force) considers various aspects of these three elements. The resources they use to develop the discussion can come from a traditional approach to strategy or from non-traditional means (e.g., so-called serious play, creativity and imagination techniques).
The S-uFunk 2.1.0 Model wants to understand to which extent cognitive means triggered by traditional and non-traditional resources affect the making of the strategy process.
Peer reviewed Infectious diseases model for mixed-methods research chapter
Mark Moritz Ian M Hamilton Chelsea E Hunter Daniel C Peart | Published Sunday, January 30, 2022The purpose of this curricular model is to teach students the basics of modeling complex systems using agent-based modeling. It is a simple SIR model that simulates how a disease spreads through a population as its members change from susceptible to infected to recovered and then back to susceptible. The dynamics of the model are such that there are multiple emergent outcomes depending on the parameter settings, initial conditions, and chance.
The curricular model can be used with the chapter Agent-Based Modeling in Mixed Methods Research (Moritz et al. 2022) in the Handbook of Teaching Qualitative & Mixed Methods (Ruth et al. 2022).
The instructional videos can be accessed on YouTube: Video 1 (https://youtu.be/32_JIfBodWs); Video 2 (https://youtu.be/0PK_zVKNcp8); and Video 3 (https://youtu.be/0bT0_mYSAJ8).
An Agent-Based Model of Indirect Minority Influence on Social Change
Jiin Jung | Published Wednesday, February 05, 2025This model demonstrates how different psychological mechanisms and network structures generate various patterns of cultural dynamics including cultural diversity, polarization, and majority dominance, as explored by Jung, Bramson, Crano, Page, and Miller (2021). It focuses particularly on the psychological mechanisms of indirect minority influence, a concept introduced by Serge Moscovici (1976, 1980)’s genetic model of social influence, and validates how such influence can lead to social change.
Peer reviewed Share: bottom-up disaster information management
Vittorio Nespeca Tina Comes Frances Brazier | Published Monday, December 05, 2022This model is intended to study the way information is collectively managed (i.e. shared, collected, processed, and stored) in a system and how it performs during a crisis or disaster. Performance is assessed in terms of the system’s ability to provide the information needed to the actors who need it when they need it. There are two main types of actors in the simulation, namely communities and professional responders. Their ability to exchange information is crucial to improve the system’s performance as each of them has direct access to only part of the information they need.
In a nutshell, the following occurs during a simulation. Due to a disaster, a series of randomly occurring disruptive events takes place. The actors in the simulation need to keep track of such events. Specifically, each event generates information needs for the different actors, which increases the information gaps (i.e. the “piles” of unaddressed information needs). In order to reduce the information gaps, the actors need to “discover” the pieces of information they need. The desired behavior or performance of the system is to keep the information gaps as low as possible, which is to address as many information needs as possible as they occur.
Peer reviewed Garbage can model Excel reconstruction
Smarzhevskiy Ivan | Published Tuesday, August 19, 2014 | Last modified Tuesday, July 30, 2019Reconstruction of the original code M. Cohen, J. March, and J. Olsen garbage can model, realized by means of Microsoft Office Excel 2010
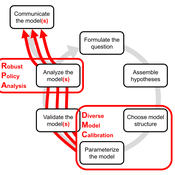
DMC-RPA: Diverse Model Calibration for Robust Policy Analysis (applied to an ABM of smallholder farmer resilience)
Tim Williams | Published Sunday, August 30, 2020This repository contains: (1) a model calibration procedure that identifies a set of diverse, plausible models; and (2) an ABM of smallholder agriculture, which is used as a case study application for the calibration method. By identifying a set of diverse models, the calibration method attends to the issue of “equifinality” prevalent in complex systems, which is a situation where multiple plausible process descriptions exist for a single outcome.
Interplay between stakeholders of the management of a river
Christophe Sibertin-Blanc Pascal Roggero Bertrand Baldet | Published Wednesday, November 12, 2014This model describes and analyses the outcomes of the confrontation of interests, some conflicting, some common, about the management of a small river in SW France
Value Chain Marketing (VCM)
Stephanie Hintze | Published Monday, April 14, 2014 | Last modified Thursday, October 16, 2014Inspired by the SKIN model, the basic concept here is to model the acceptance and implementation of supplier innovations. This model includes three types of agents comprising suppliers, manufacturers and applicators.
Peer reviewed JuSt-Social COVID-19
Jennifer Badham | Published Thursday, June 18, 2020 | Last modified Monday, March 29, 2021NetLogo model that allows scenarios concerning general social distancing, shielding of high-risk individuals, and informing contacts when symptomatic. Documentation includes a user manual with some simple scenarios, and technical information including descriptions of key procedures and parameter values.
Epidemic Simulation with Transportation Simulation
FG Econophysics FG Econophysics | Published Monday, March 01, 2021The Episim framework builds upon the established transportation simulation MATSim and is capable of tracking agents’ movements within a network and thus computing infection chains. Several characteristics of the virus and the environment can be parametred, whilst the infection dynamics is computed based upon a compartment model. The spread of the virus can be mitigated by restricting the agents’ activity in certain places.
Displaying 10 of 1170 results for "Aad Kessler" clear search