About the CoMSES Model Library more info
Our mission is to help computational modelers develop, document, and share their computational models in accordance with community standards and good open science and software engineering practices. Model authors can publish their model source code in the Computational Model Library with narrative documentation as well as metadata that supports open science and emerging norms that facilitate software citation, computational reproducibility / frictionless reuse, and interoperability. Model authors can also request private peer review of their computational models. Models that pass peer review receive a DOI once published.
All users of models published in the library must cite model authors when they use and benefit from their code.
Please check out our model publishing tutorial and feel free to contact us if you have any questions or concerns about publishing your model(s) in the Computational Model Library.
We also maintain a curated database of over 7500 publications of agent-based and individual based models with detailed metadata on availability of code and bibliometric information on the landscape of ABM/IBM publications that we welcome you to explore.
Displaying 10 of 549 results for "Niklas Hase" clear search
00 PSoup V1.22 – Primordial Soup
Garvin Boyle | Published Thursday, April 13, 2017PSoup is an educational program in which evolution is demonstrated, on the desk-top, as you watch. Blind bugs evolve sophisticated heuristic search algorithms to be the best at finding food fast.
Peer reviewed MADTOR: Model for Assessing Drug Trafficking Organizations Resilience
Deborah Manzi | Published Friday, February 23, 2024Criminal organizations operate in complex changing environments. Being flexible and dynamic allows criminal networks not only to exploit new illicit opportunities but also to react to law enforcement attempts at disruption, enhancing the persistence of these networks over time. Most studies investigating network disruption have examined organizational structures before and after the arrests of some actors but have disregarded groups’ adaptation strategies.
MADTOR simulates drug trafficking and dealing activities by organized criminal groups and their reactions to law enforcement attempts at disruption. The simulation relied on information retrieved from a detailed court order against a large-scale Italian drug trafficking organization (DTO) and from the literature.
The results showed that the higher the proportion of members arrested, the greater the challenges for DTOs, with higher rates of disrupted organizations and long-term consequences for surviving DTOs. Second, targeting members performing specific tasks had different impacts on DTO resilience: targeting traffickers resulted in the highest rates of DTO disruption, while targeting actors in charge of more redundant tasks (e.g., retailers) had smaller but significant impacts. Third, the model examined the resistance and resilience of DTOs adopting different strategies in the security/efficiency trade-off. Efficient DTOs were more resilient, outperforming secure DTOs in terms of reactions to a single, equal attempt at disruption. Conversely, secure DTOs were more resistant, displaying higher survival rates than efficient DTOs when considering the differentiated frequency and effectiveness of law enforcement interventions on DTOs having different focuses in the security/efficiency trade-off.
Overall, the model demonstrated that law enforcement interventions are often critical events for DTOs, with high rates of both first intention (i.e., DTOs directly disrupted by the intervention) and second intention (i.e., DTOs terminating their activities due to the unsustainability of the intervention’s short-term consequences) culminating in dismantlement. However, surviving DTOs always displayed a high level of resilience, with effective strategies in place to react to threatening events and to continue drug trafficking and dealing.
Wedding Doughnut
Eric Silverman Jason Hilton Jakub Bijak Viet Cao | Published Thursday, December 20, 2012 | Last modified Friday, September 20, 2013A reimplementation of the Wedding Ring model by Francesco Billari. We investigate partnership formation in an agent-based framework, and combine this with statistical demographic projections using real empirical data.
The Garbage Can Model of Organizational Choice
Guido Fioretti | Published Saturday, June 22, 2013We reconstruct Cohen, March and Olsen’s Garbage Can model of organizational choice as an agent-based model. We add another means for avoiding making decisions: buck-passing difficult problems to colleagues.
Peer reviewed Ideal Free Distribution of Mobile Pastoralists in the Logone Floodplain, Cameroon
Jeff Cronley Andrew Yoak Mark Moritz Hongyang Pi Ian M Hamilton Paul Maddock | Published Thursday, June 19, 2014 | Last modified Saturday, January 06, 2018The purpose of the model is to examine whether and how mobile pastoralists are able to achieve an Ideal Free Distribution (IFD).
Charcoal Record Simulation Model (CharRec)
Grant Snitker | Published Monday, November 16, 2015 | Last modified Thursday, September 30, 2021This model (CharRec) creates simulated charcoal records, based on differing natural and anthropogenic patterns of ignitions, charcoal dispersion, and deposition.
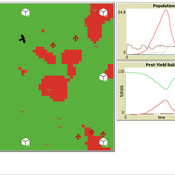
Peer reviewed Avian pest control: Yield outcome due to insectivorous birds, falconry, and integration of nest boxes.
David Jung | Published Monday, November 13, 2023 | Last modified Sunday, November 19, 2023The model aims to simulate predator-prey relationships in an agricultural setting. The focus lies on avian communities and their effect on different pest organisms (here: pest birds, rodents, and arthropod pests). Since most case studies focused on the impact on arthropod pests (AP) alone, this model attempts to include effects on yield outcome. By incorporating three treatments with different factor levels (insectivorous bird species, falconry, nest box density) an experimental setup is given that allows for further statistical analysis to identify an optimal combination of the treatments.
In light of a global decline of birds, insects, and many other groups of organisms, alternative practices of pest management are heavily needed to reduce the input of pesticides. Avian pest control therefore poses an opportunity to bridge the disconnect between humans and nature by realizing ecosystem services and emphasizing sustainable social ecological systems.
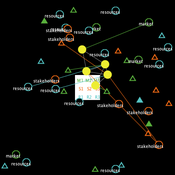
Peer reviewed Visibility of archaeological social networks
Claudine Gravel-Miguel | Published Sunday, November 26, 2023The purpose of this model is to explore the impact of combining archaeological palimpsests with different methods of cultural transmission on the visibility of prehistoric social networks. Up until recently, Paleolithic archaeologists have relied on stylistic similarities of artifacts to reconstruct social networks. However, this method - which is successfully applied to more recent ceramic assemblages - may not be applicable to Paleolithic assemblages, as several of those consist of palimpsests of occupations. Therefore, this model was created to study how palimpsests of occupation affect our social network reconstructions.
The model simplifies inter-groups interactions between populations who share cultural traits as they produce artifacts. It creates a proxy archaeological record of artifacts with stylistic traits that can then be used to reconstruct interactions. One can thus use this model to compare the networks reconstructed through stylistic similarities with direct contact.
The S-uFUNK Model
Davide Secchi | Published Friday, March 17, 2023This version 2.1.0 of the uFunk model is about setting a business strategy (the S in the name) for an organization. A team of managers (or executives) meet and discuss various options on the strategy for the firm. There are three aspects that they have to agree on to set the strategic positioning of the organization.
The discussion is on market, stakeholders, and resources. The team (it could be a business strategy task force) considers various aspects of these three elements. The resources they use to develop the discussion can come from a traditional approach to strategy or from non-traditional means (e.g., so-called serious play, creativity and imagination techniques).
The S-uFunk 2.1.0 Model wants to understand to which extent cognitive means triggered by traditional and non-traditional resources affect the making of the strategy process.
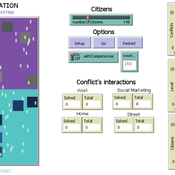
Citizenship competences and conflict resolution styles
Cecilia Avila Manuel Balaguera Valentina Tabares | Published Monday, February 03, 2020This model represents an agent-based social simulation for citizenship competences. In this model people interact by solving different conflicts and a conflict is solved or not considering two possible escenarios: when individual citizenship competences are considered and when not. In both cases the TKI conflict resolution styles are considered. Each conflict has associated a competence and the information about the conflicts and their competences is retrieved from an ontology which was developed in Protégé. To do so, a NetLogo extension was developed using the Java programming language and the JENA API (to make queries over the ontology).
Displaying 10 of 549 results for "Niklas Hase" clear search