About the CoMSES Model Library more info
Our mission is to help computational modelers develop, document, and share their computational models in accordance with community standards and good open science and software engineering practices. Model authors can publish their model source code in the Computational Model Library with narrative documentation as well as metadata that supports open science and emerging norms that facilitate software citation, computational reproducibility / frictionless reuse, and interoperability. Model authors can also request private peer review of their computational models. Models that pass peer review receive a DOI once published.
All users of models published in the library must cite model authors when they use and benefit from their code.
Please check out our model publishing tutorial and feel free to contact us if you have any questions or concerns about publishing your model(s) in the Computational Model Library.
We also maintain a curated database of over 7500 publications of agent-based and individual based models with detailed metadata on availability of code and bibliometric information on the landscape of ABM/IBM publications that we welcome you to explore.
Displaying 10 of 88 results for "Carlos Franco" clear search
Hybrid agent-based methodology for testing response protocols
Fernando Sancho Caparrini | Published Wednesday, February 03, 2021In recent years we have seen multiple incidents with a large number of people injured and killed by one or more armed attackers. Since this type of violence is difficult to predict, detecting threats as early as possible allows to generate early warnings and reduce response time. In this context, any tool to check and compare different action protocols can be a further step in the direction of saving lives. Our proposal combines features from continuous and discrete models to obtain the best of both worlds in order to simulate large and crowded spaces where complex behavior individuals interact. With this proposal we aim to provide a tool for testing different security protocols under several emergency scenarios, where spaces, hazards, and population can be customized. Finally, we use a proof of concept implementation of this model to test specific security protocols under emergency situations for real spaces. Specifically, we test how providing some users of a university college with an app that informs about the type and characteristics of the ongoing hazard, affects in the safety performance.
Agent-based Line-of-Sight Simulation for safer Crossings (Short Paper - Netlogo Model)
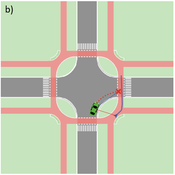
Vincent Franke | Published Thursday, August 05, 2021This software simulates cars and bicycles as traffic participants while crossing different crossroad designs such as roundabouts, protected crossroads and standard crossroads. It is written in Netlogo 6.2 and aims to identify safety characteristics of these layouts using agent-based modeling. Participants track the line of sight to each other and print them as an output alongside with the adjacent destination, used layout, count of collisions/cars/bicycles and time.
Detailed information can be found within the info tab of the program itself.
SAFARI: Simulating Agroforestry Adoption in Rural Indonesia
Beatrice Nöldeke Etti Winter Yves Laumonier Trifosa Simamora | Published Tuesday, July 20, 2021The Simulating Agroforestry Adoption in Rural Indonesia (SAFARI) model aims at exploring the adoption of illipe rubber agroforestry systems by farming households in the case study region in rural Indonesia. Thereby, the ABM simulates the interdependencies of agroforestry systems and local livelihoods, income, land use, biodiversity, and carbon fixation. The model contrasts development paths without agroforestry (business as usual (BAU) scenario), corresponding to a scenario where the government promotes rubber monoculture, with the introduction of illipe rubber agroforestry systems (IRA scenario) as an alternative. It aims to support policy-makers to assess the potential of IRA over larger temporal and spatial scales.
Alternative scenarios of green consumption in Italy: an empirically grounded model.
Giangiacomo Bravo Elena Vallino Alessandro K Cerutti Maria Beatrice Pairotti | Published Thursday, March 28, 2013 | Last modified Saturday, April 27, 2013We provide a full description of the model following the ODD protocol (Grimm et al. 2010) in the attached document. The model is developed in NetLogo 5.0 (Wilenski 1999).
Two agent-based models of cooperation in dynamic groups and fixed social networks
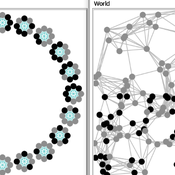
Carlos A. de Matos Fernandes | Published Thursday, January 20, 2022Both models simulate n-person prisoner dilemma in groups (left figure) where agents decide to C/D – using a stochastic threshold algorithm with reinforcement learning components. We model fixed (single group ABM) and dynamic groups (bad-barrels ABM). The purpose of the bad-barrels model is to assess the impact of information during meritocratic matching. In the bad-barrels model, we incorporated a multidimensional structure in which agents are also embedded in a social network (2-person PD). We modeled a random and homophilous network via a random spatial graph algorithm (right figure).
STECCAR: a simulation of the diffusion of electric cars
A Kangur Lc Verbrugge W Jager M Bockarjova | Published Sunday, November 29, 2015In this Repast model the ‘Consumat’ cognitive framework is applied to an ABM of the Dutch car market. Different policy scenarios can be selected or created to examine their effect on the diffusion of EVs.
Modelling an intersection with traffic signal countdown timer
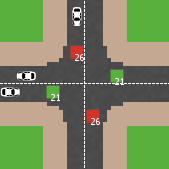
Eduard | Published Thursday, May 19, 2022Developed as a part of a project in the University of Augsburg, Institute of Geography, it simulates the traffic in an intersection or junction which uses either regular traffic lights or traffic lights with a countdown timer. The model tracks the average speed of cars before and after traffic lights as well as the throughput.
A simple emulation-based computational model
Carlos M Fernández-Márquez Francisco J Vázquez | Published Tuesday, May 21, 2013 | Last modified Tuesday, February 05, 2019Emulation is one of the simplest and most common mechanisms of social interaction. In this paper we introduce a descriptive computational model that attempts to capture the underlying dynamics of social processes led by emulation.
Sunshine or Shield?: Secret Voting Procedures and Legislative Accountability
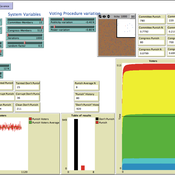
Matthew Taylor Michele Buttò Carlos Pereira | Published Tuesday, June 24, 2014 | Last modified Monday, April 08, 2019An agent-based model is used to simulate legislators’ behavior under secret voting rules, as influenced by the power of the accused politician, the composition of the voting body, and the publicity of the accusations.
Rebel Group Protection Rackets
Gerd Wagner Luis Gustavo Nardin Kamil C. Klosek Frances Duffy | Published Wednesday, December 04, 2019System Narrative
How do rebel groups control territory and engage with the local economy during civil war? Charles Tilly’s seminal War and State Making as Organized Crime (1985) posits that the process of waging war and providing governance resembles that of a protection racket, in which aspiring governing groups will extort local populations in order to gain power, and civilians or businesses will pay in order to ensure their own protection. As civil war research increasingly probes the mechanisms that fuel local disputes and the origination of violence, we develop an agent-based simulation model to explore the economic relationship of rebel groups with local populations, using extortion racket interactions to explain the dynamics of rebel fighting, their impact on the economy, and the importance of their economic base of support. This analysis provides insights for understanding the causes and byproducts of rebel competition in present-day conflicts, such as the cases of South Sudan, Afghanistan, and Somalia.
Model Description
The model defines two object types: RebelGroup and Enterprise. A RebelGroup is a group that competes for power in a system of anarchy, in which there is effectively no government control. An Enterprise is a local civilian-level actor that conducts business in this environment, whose objective is to make a profit. In this system, a RebelGroup may choose to extort money from Enterprises in order to support its fighting efforts. It can extract payments from an Enterprise, which fears for its safety if it does not pay. This adds some amount of money to the RebelGroup’s resources, and they can return to extort the same Enterprise again. The RebelGroup can also choose to loot the Enterprise instead. This results in gaining all of the Enterprise wealth, but prompts the individual Enterprise to flee, or leave the model. This reduces the available pool of Enterprises available to the RebelGroup for extortion. Following these interactions the RebelGroup can choose to AllocateWealth, or pay its rebel fighters. Depending on the value of its available resources, it can add more rebels or expel some of those which it already has, changing its size. It can also choose to expand over new territory, or effectively increase its number of potential extorting Enterprises. As a response to these dynamics, an Enterprise can choose to Report expansion to another RebelGroup, which results in fighting between the two groups. This system shows how, faced with economic choices, RebelGroups and Enterprises make decisions in war that impact conflict and violence outcomes.
Displaying 10 of 88 results for "Carlos Franco" clear search